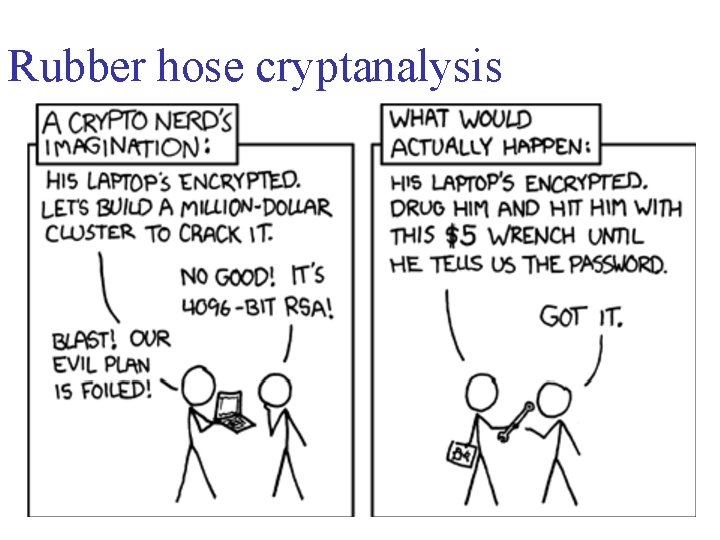
Anonymous Ghostwriters - Rubber Hose Cryptography works by filling the entire hard drive with random characters that are indistinguishable from encrypted data. The file system then takes each archive of real data

Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks A Paper by Hristo Bojinov, Daniel Sanchez, Paul Reber, - ppt download

Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks | USENIX